RAG Security in the Age of DeepSeek: Building Safe Enterprise Knowledge Systems
As DeepSeek advances, securing retrieval-augmented generation (RAG) systems is crucial. Learn how enterprises can build safe, resilient knowledge systems by implementing robust security measures to protect sensitive data and ensure trustworthy AI-driven insights.

Imagine this: the systems designed to safeguard enterprise knowledge can potentially become the weakest link in your security chain.
Retrieval-Augmented Generation (RAG) systems, blending generative AI with real-time data retrieval, are revolutionizing business intelligence—but at a cost.
Without robust safeguards, they can leak sensitive data, invite adversarial attacks, and create compliance nightmares.
With the rapid adoption of open-source models like DeepSeek R1, organizations must ask one critical question: how do you balance the power of real-time retrieval with airtight security?
This article dives into the untapped intersection of RAG technology and enterprise security, offering actionable insights to help you build systems that are not just intelligent but also impervious to modern threats.
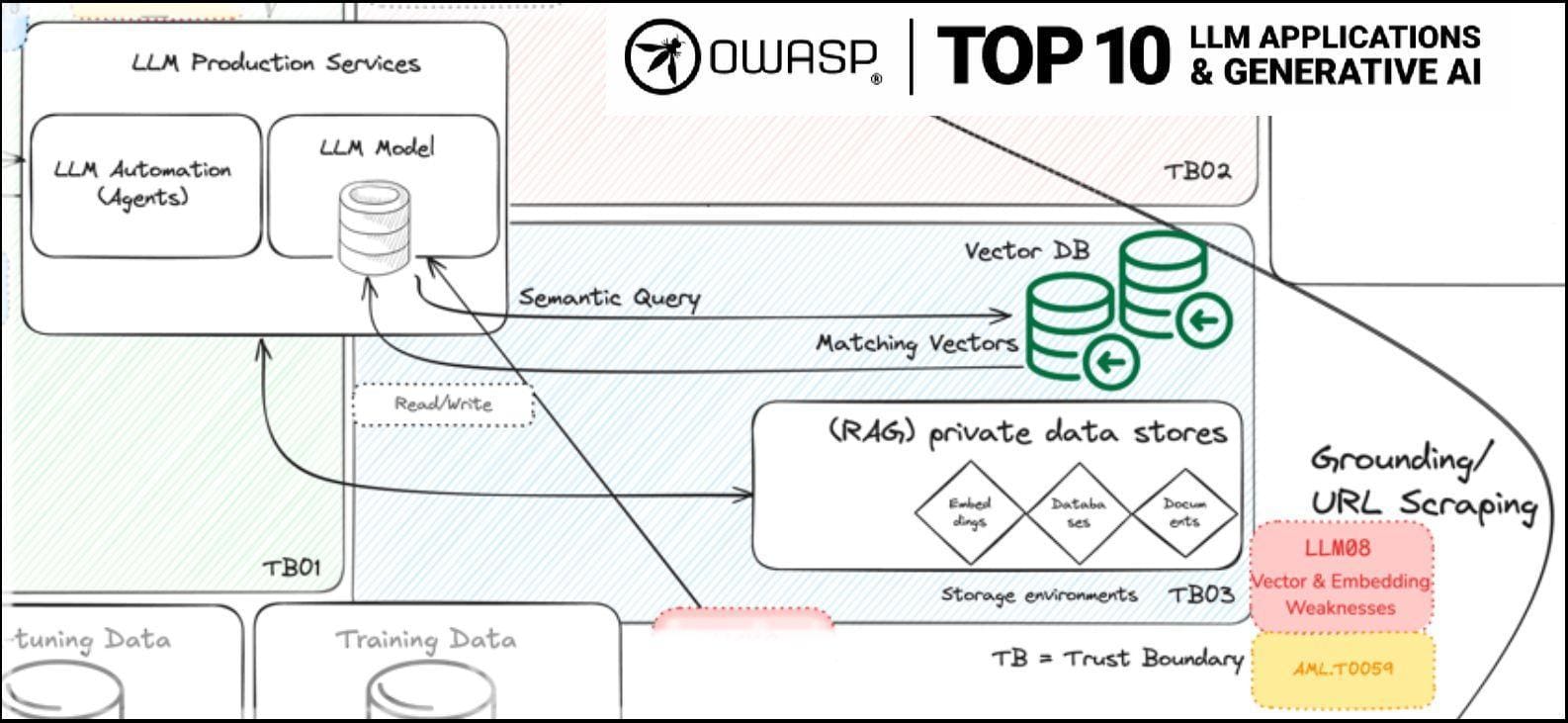
The Imperative for Secure Retrieval-Augmented Generation
Let’s talk about vector database security—a critical yet often overlooked aspect of RAG systems.
These databases, like Pinecone or ChromaDB, store embeddings that power retrieval.
However, embeddings can inadvertently leak sensitive data. For example, adversarial actors could reverse-engineer embeddings to extract confidential information.
So, how do you protect them?
Start with encryption at rest and in transit. This ensures that even if the database is compromised, the data remains unreadable.
Next, implement role-based access controls. Only authorized users should query embeddings, and even then, access should be limited to specific roles.
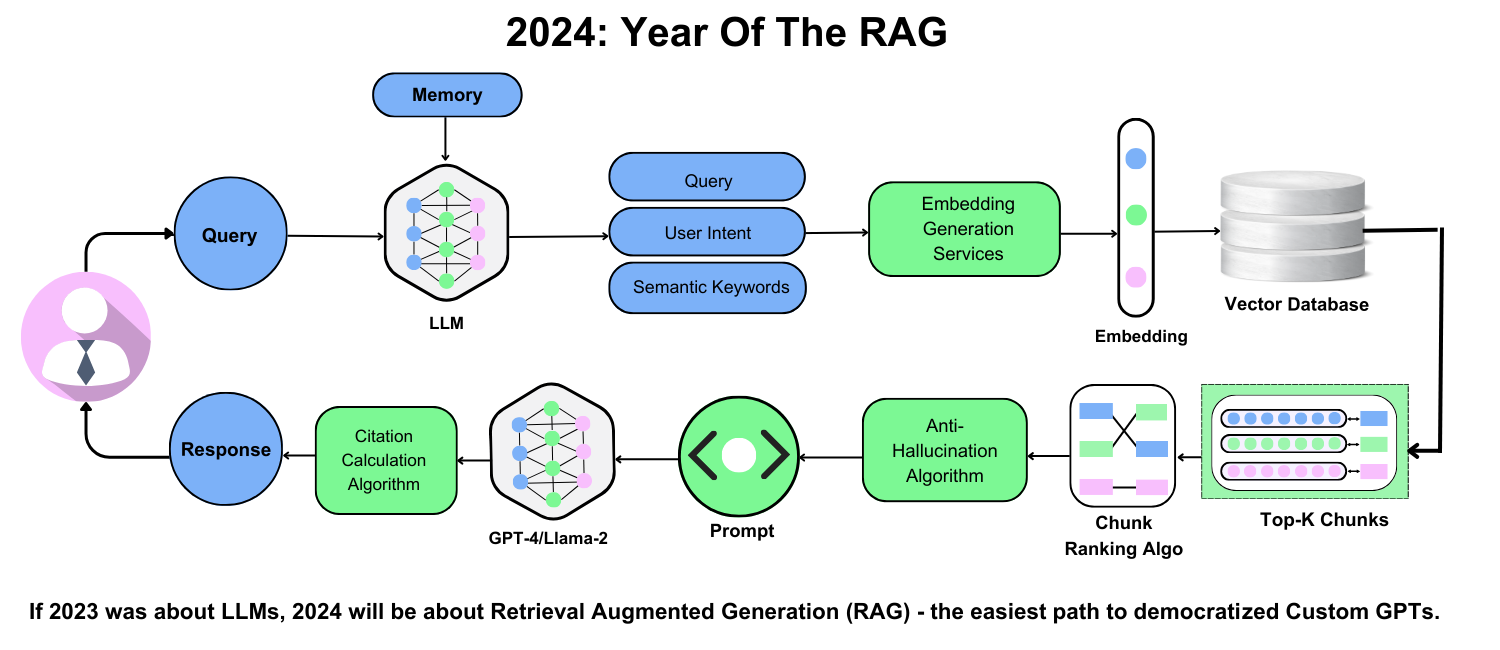
Understanding Retrieval-Augmented Generation (RAG)
Let’s talk about adaptive retrieval, a feature that sets advanced RAG systems apart.
Unlike static retrieval methods, adaptive retrieval dynamically adjusts its search parameters based on the query’s complexity and context.
Why does this matter? Because in high-stakes industries like finance or healthcare, precision isn’t optional—it’s critical.
Take fraud detection in banking. A RAG system with adaptive retrieval doesn’t just pull transaction data; it prioritizes anomalies based on real-time patterns, flagging risks faster than traditional systems.
This approach blends machine learning with domain-specific heuristics, creating a feedback loop that improves over time.
DeepSeek: Features and Innovations
One standout feature of DeepSeek R1 is its chain-of-thought methodology, which transforms how AI systems reason and retrieve data.
Unlike black-box models, DeepSeek R1 makes its reasoning process transparent, showing every step it takes to conclude.
This isn’t just a technical novelty—it’s a game-changer for industries like healthcare and finance, where trust and compliance are non-negotiable.
Security Challenges in RAG Systems
RAG systems are like vaults of enterprise knowledge—but even vaults have vulnerabilities. One major challenge? Data leakage. Imagine a healthcare RAG system accidentally exposing patient records during a query. This isn’t hypothetical; studies show RAG systems can unintentionally retrieve sensitive data if not properly secured.
And let’s not forget access control gaps. Without strict role-based permissions, even internal users might access data they shouldn’t. A finance team member retrieving R&D prototypes? That’s a compliance nightmare waiting to happen.
The solution? Encryption, zero-trust architectures, and constant monitoring. These aren’t just buzzwords—they’re the guardrails keeping your RAG system from becoming a liability.

Common Vulnerabilities in RAG Implementations
One overlooked vulnerability in RAG systems is oversharing through vector embeddings.
Unlike raw data, embeddings are often treated as harmless abstractions. But here’s the catch: attackers can reverse-engineer embeddings to reconstruct sensitive information.
For instance, inversion attacks on healthcare embeddings have revealed patient diagnoses—turning a supposed safeguard into a liability.
To mitigate these risks, enterprises should adopt privacy-preserving retrieval techniques like federated learning and enforce attribute-based access controls (ABAC).
These measures ensure embeddings remain secure and retrieval respects contextual boundaries.
Threat Models Specific to DeepSeek Integration
When integrating DeepSeek into RAG systems, prompt injection attacks deserve focused attention.
These attacks exploit the model’s reliance on user-provided inputs, embedding malicious instructions that manipulate outputs or expose sensitive data.
For example, in a healthcare RAG system, an attacker could craft a query that bypasses access controls, retrieving confidential patient records.
It happens due to DeepSeek’s “chain-of-thought” methodology. While transparent, it can inadvertently amplify vulnerabilities by exposing intermediate reasoning steps.
Attackers can analyze these steps to refine their exploits, making traditional defenses like static input validation insufficient.
Architecting Secure RAG Systems with DeepSeek
Building a secure RAG system with DeepSeek R1 is like designing a fortress—every layer must be fortified. Start with fine-grained access controls.
Think of it as issuing keys to only those who need them. For example, SpiceDB can enforce role-based permissions, ensuring sensitive data stays locked away from unauthorized users.
Finally, don’t underestimate prompt sanitization. Malicious queries can act like Trojan horses, sneaking into your system. DeepSeek’s dynamic prompt filtering is a game-changer here, blocking threats before they cause damage.

Best Practices for System Design
When designing a secure RAG system, adaptive retrieval optimization deserves special attention.
Instead of treating all queries equally, systems should dynamically adjust retrieval parameters based on context.
For instance, in healthcare, a query about “patient history” should prioritize recent, high-relevance data while excluding unrelated records. This not only improves accuracy but also minimizes exposure to sensitive information.
Data Encryption and Secure Storage Solutions
When it comes to securing RAG systems, homomorphic encryption is a game-changer.
Unlike traditional encryption, it allows computations on encrypted data without decrypting it.
This means sensitive embeddings in vector databases can remain secure even during processing.
However, homomorphic encryption is computationally expensive. To balance security and performance, enterprises can adopt hybrid encryption models.
These combine homomorphic encryption for critical operations with faster symmetric encryption for less sensitive tasks. This layered approach optimizes both speed and security.

Anomaly Detection and AI-driven Threat Monitoring
Anomaly detection in RAG systems isn’t just about spotting the obvious. It’s about identifying minor deviations in query patterns or data retrieval behaviors that could signal a brewing attack.
For instance, DeepSeek R1 can integrate with AI-driven tools like Prometheus or Splunk to monitor real-time anomalies in retrieval requests, flagging unusual access attempts before they escalate.
What makes this approach powerful is its ability to correlate anomalies across multiple layers—from user behavior to system-level metrics. Imagine a scenario where a sudden spike in retrieval volume coincides with unusual query phrasing. By combining these signals, AI can pinpoint potential adversarial retrieval attempts with surgical precision.
Compliance with Regulatory Standards
Let’s zero in on data subject rights—a cornerstone of regulations like GDPR and CCPA.
These rights empower users to access, delete, or transfer their data, but implementing them in RAG systems is no small feat.
Why? Because RAG systems often pull data from multiple sources, making it tricky to track and manage individual data points.
One effective approach is dynamic data tagging. By tagging data with metadata about its origin, purpose, and user permissions, organizations can automate compliance processes.
For instance, a financial institution could instantly locate and delete a customer’s data upon request, avoiding hefty fines.
FAQ
What are the key security challenges faced by RAG systems in enterprise environments?
RAG systems face data leakage, unauthorized access, prompt injection attacks, and adversarial retrieval threats. Attackers can manipulate embeddings, extract sensitive data, or overload systems with complex queries. Multi-layered security measures, including encryption, access controls, and monitoring, are essential.
How does DeepSeek enhance the security of Retrieval-Augmented Generation systems?
DeepSeek improves security with transparent reasoning, real-time prompt sanitization, encryption, and fine-grained access controls. Its adaptive retrieval minimizes exposure to sensitive data while maintaining accuracy. Centralized logging and monitoring detect anomalies and prevent breaches.
What best practices should organizations follow to secure vector databases in RAG systems?
Use RBAC or ABAC for access control, encrypt data at rest and in transit, and limit user permissions. Regular security audits, query validation, and key management prevent unauthorized access. Anonymization and data isolation enhance protection against breaches.
How can dynamic threat modeling and zero-trust architectures improve RAG system security?
Dynamic threat modeling detects vulnerabilities in real-time, while zero-trust enforces continuous verification. Micro-segmentation and granular access controls prevent lateral attacks. Together, they create a proactive defense framework for RAG systems.
What role does encryption play in safeguarding sensitive data within RAG pipelines?
Encryption ensures confidentiality, integrity, and compliance in RAG pipelines. Techniques like homomorphic encryption secure embeddings during processing. Key management and multi-layered encryption strategies protect sensitive data from breaches.
Final Thoughts on Ensuring Secure Enterprise Knowledge Systems
Building secure RAG systems in the age of DeepSeek is like constructing a fortress with transparent walls—balancing visibility and protection.
While DeepSeek R1's transparency fosters trust, it also demands rigorous safeguards to prevent vulnerabilities from being exploited.
Looking ahead, enterprises must embrace adaptive, interdisciplinary frameworks to stay ahead of evolving threats.

